News
BIECO Impact: The project concept is designed to provide benefits for industrial partners on both short and long term. On short term, the industrial partners will receive innovative technologies and set of methods/tools to support security and resilience within their supply chains; on the long term, the functionality of the technologies will be applicable to build new secure and resilient ecosystems, opening new business possibilities.
REVIEW MEETING M18 – 29th April, 2022
Friday 29th April 2022 - 13.00 – 17.00 CET AGENDA Overview 13:00 - 13:10 Project Overview 13:10 - 15:10 WP2 - WP9 Presentations 15:10 - 15:20 Break 15:20 - 15:50 BIECO Demo 15:50 - 16:00 BIECO Use Cases 16:00 - 16:15 Project Coordination and Management 16:15 -...
The Need for IoT Security Standards & Certification Global IoT Day Roundtable – Recording available
If you missed the chance to attend to the Global IoT Roundtable about the need for IoT security standards and certification, you can watch the recording of the sessions in YouTube. Session 1: Organizations (DG CNECT, ENISA, ETSI, ECSO, GlobalPlatform, AIOTI, E&Y,...
The BIECO video presentation M18
The BIECO video presentation M18The BIECO presentation In the light of fast development of cyber threats, the complexity of heterogenous ICT ecosystems raise major security concerns. In this regard, BIECO provides a set of tools and methodologies for building...

The need for IoT security standards & certification
IoT Day Roundtable – 8. April 2022 WHAT SHOULD YOU KNOW ABOUT PROSPECTIVE EUROPEAN IOT SECURITY STANDARDS AND CERTIFICATION? ARE YOU PREPARED FOR A NEW ERA?To celebrate Global IoT Day, we are organizing an online roundtable with the participation...
BIECO, un approccio olistico alla cybersecurity (BIECO and holistic approach for the cybersecurity)
BIECO, un approccio olistico alla cybersecurity (BIECO and holistic approach for the cybersecurity) Author: Eda Marchetti Document type: Other Publisher: Italian newspaper “il sole 24 ore” special insert “SCENARI” daily (published 28th of February 2022)
The GDPR Compliance and Access Control Systems: Challenges and Research Opportunities
The GDPR Compliance and Access Control Systems: Challenges and Research Opportunities Authors: Said Daoudagh, Eda Marchetti Document type: Publication in Conference proceedings Publication: Proceedings of the 8th International Conference on Information Systems...
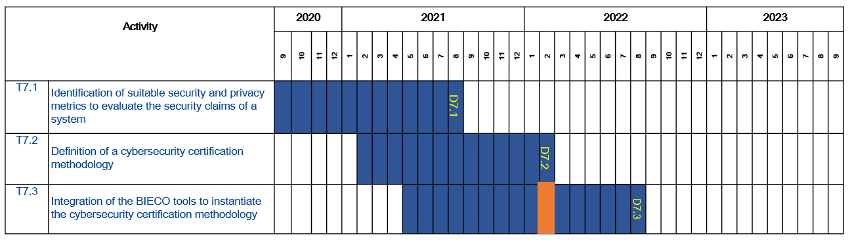
WP7 monthly meeting M18
WP7 has closed its second task, finishing the security evaluation methodology that is intended to be instantiated in the last task of the WP. Currently, we are working very hard on the demo for the project intermediate review in which we will show pieces of the...
WP7 monthly meeting M17
In the monthly meeting of 10th January, WP7 is working on the security evaluation methodology that should be finished by next month. We are reviewing the details of the deliverable that will contain all the information about the methodology. Regarding T7.3, 7bulls...

WP8 Monthly Meeting
WP8 Monthly MeetingOn 7th of December 2021 WP8 partners have gathered for the regular monthly meeting of the work package. Some aspects were defined, like what endpoints will the tools use in relation with the orchestrator, and the initial architecture of the...
WP6 monthly meeting M16
The 6th December took place the WP6 monthly meeting. During the meeting IESE summarized the status of T6.3 and D6.4. Additional enhancements to the T6.3 activities and further work were discussed. 7Bulls updated on the status of their tool and use case, and discussed...

Workshop “FUTURE PROOFING AND CERTIFYING SUPPLY CHAINS”
The Clustering Workshop co-organized by EU-funded projects ASSURED, and CYRENE aims at bringing together projects that target Supply Chain Security, Resilience and Certification aspects, experts, members and consultants from standardization and certification bodies...
BIECO brochure
BIECO-brochure-1Download

