BIECO
The general objective of BIECO is to develop a framework that enables measurable, risk-based trust while developing, deploying and operating complex interconnected ICT systems.
Objectives
We aim to achieve this by handling the reliability and trust aspects of ecosystem participants (ICT systems, ICT system components and actors) within the supply chain.
The following shows the specific SMART (Specific, Measurable, Achievable, Realistic, Time-bound) objectives of the project, taking into account the challenges of this kind of complex ecosystems.
Framework
Providing a framework that allows reinforcing trust in ICT supply chains (WP2).
Vulnerability assessment
Performing advanced vulnerability assessment over ICT supply chains (WP3).
Achieving resilience
Achieving resilience in ecosystems formed by unreliable components (WP4).
Extending auditing
Extending auditing process to evaluate interconnected ICT systems (WP5).
Advanced risk analysis
Provide advanced risk analysis and mitigation strategies that support a view of the complete ICT supply chain (WP6).
Security assurance
Perform evidence-based security assurance and a harmonized certification for ICT systems (WP7).
Industrial validation
Industrial validation of BIECO’s framework within IoT ecosystems (WP8).
Exploitable Results
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
About BIECO
The rationale behind BIECO’s concept is to deliver a framework for improving trust and security within ICT supply chains. These are complex ecosystems comprising several heterogeneous technologies, processes, actors (e.g., end-users, software or hardware providers and organizations) and resources, all of which generate or exchange data forming extremely complex information management systems.
The BIECO team is proud to announce

NEWS

A comparative study of the most important methods for forecasting the ICT systems vulnerabilities
A comparative study of the most important methods for forecasting the ICT systems vulnerabilities Publication in Conference proceedings/Workshop Authors: Ovidiu Cosma, Mara Hajdu-Macelaru, Petrica Pop-Sitar, Cosmin Sabo, Ioana Zelina DOI: 10.1007/978-3-030-87872-6_22...

Comparison of Safety and Security analysis techniques
Title: Comparison of Safety and Security analysis techniques Authors: Emilia Cioroaica, Smruti Ranjan Kar, and Ioannis Sorokos Document type: Publication in Conference proceedings Publication info: CISIS 2021 Conference http://2021.cisisconference.eu/ DOI:...
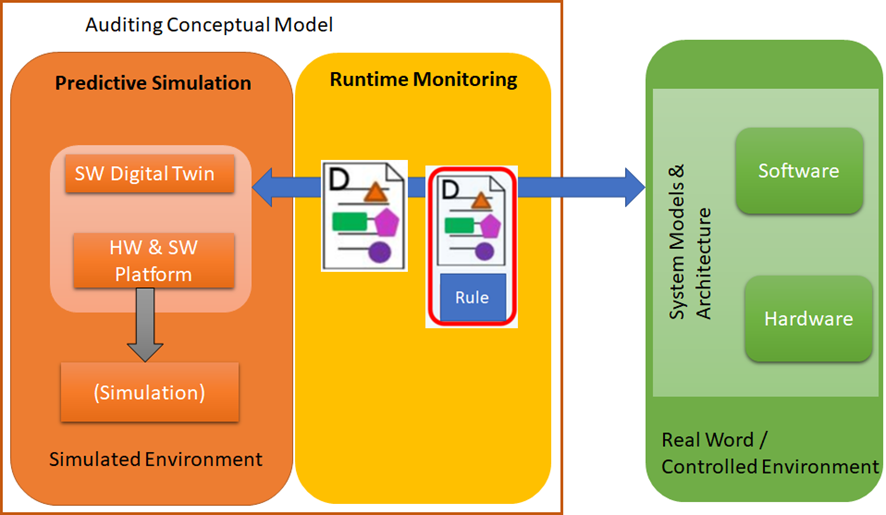
BIECO Runtime Auditing Framework
Title: BIECO Runtime Auditing Framework Publication info: CISIS 2021 Conference http://2021.cisisconference.eu/ Authors: Antonello Calabrò, Emilia Cioroaica, Said Daoudagh and Eda Marchetti Conference: 14th International Conference on Computational Intelligence...

Goals within Trust-based Digital Ecosystems
Title: Goals within Trust-based Digital Ecosystems Authors: Emilia Cioroaica, Akanksha Purohit, Barbora Buhnova, and Daniel Schneider Document type: Publication in Conference proceedings Publication info: 2021 IEEE/ACM Joint 9th International Workshop on Software...

Bridging Trust in Runtime Open Evaluation Scenarios
Title: Bridging Trust in Runtime Open Evaluation Scenarios Authors: Emilia Cioroaica, Barbora Buhnova, Eda Marchetti, Daniel Schneider, and Thomas Kuhn Publication info: SIAS 2021 Conference https://www.sscc.fr/SIAS2021/ Abstract: Solutions to specific challenges...

BIECO M12 Progress Meeting
BIECO M12 Progress Meeting Agenda 7-8th September 2021, 09:00- 15:00 CET Location: Teams – General Meeting Objectives: Check the progress statusAlign the work in all WP’sAlign the view of the participants with the vision of the project Attendees: Representatives of...












