Use Cases
The methodologies and tools provided by BIECO’s framework will be evaluated in four use cases from different sectors.
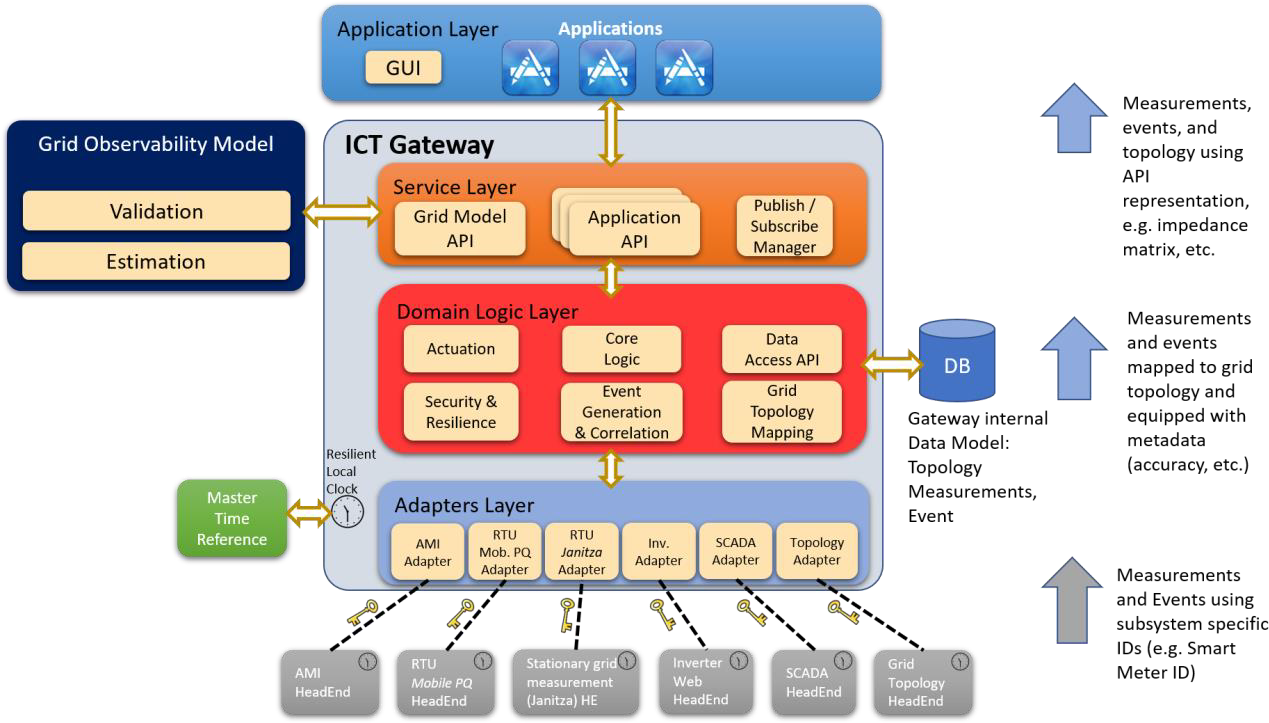
Use Case 1: ICT Gateway
The ICT gateway is a component intended for Smart Grids that acts as mediator between data sourcing and actuation subsystems and domain applications.
Use case 1
ICT Gateway: supports data and configuration/control flows for all applications, as for example applications on grid outage diagnosis, grid efficiency and voltage quality.
Its main functionalities are ICT monitoring, and early detection and diagnosis of anomalies.
The system is divided into four layers: the Adapters Layer that connects the ICT Gateway to the smart grid; the Domain Logic Layer handles interactions with actuation subsystems and contains basic attack and fault detection mechanisms; the Service Layer specifies how the ICT Gateway communicates with other components and applications; and the Application Layer that includes a GUI. Besides these layers, the gateway includes a Resilient Local Clock that implements a low-intrusive software clock in charge of synchronizing local time to a master
ICT Gateway: Technologies and methodologies
In BIECO the ITC gateway will be used to demonstrate the application of several technologies and methodologies developed in the project.
These features will allow to improve the attack and fault detection mechanisms of the software, enhancing its diagnosis capabilities thanks to the advanced security monitoring tools provided by BIECO. After detecting a malicious behavior, it will allow to trigger the necessary actions to bring the system into a safe state, avoiding hazardous situations and reducing the probability of propagation to the smart grid.
Detecting vulnerabilities
Detecting more accurately software vulnerability that might exist in the software, and determine how a possible vulnerability of the gateway could propagate to the smart grid (WP3).
Auditing and monitoring
Auditing and monitoring the integration with other third party systems and components, as well as the correct runtime behaviour of the gateway and its subsystems (WP5).
Obtaining guarantees
Obtaining guarantees that certify the adherence of the software to its expected behaviour (WP7).
Performing self-checks
Performing self-checks that allow to detect residual vulnerabilities, software and hardware failures; using simulation tools that enable a virtual evaluation when an adversary is influencing clock synchronization (WP4).
Risk assessment
Performing a risk assessment and threat modelling of the status of the system, taking into account also how a gateway vulnerability could impact the smart grid (WP6).

USE CASE 2
Investment portfolio optimization platform
Investment portfolio optimization platform
This use case aims at providing security guarantees to a Machine Learning based platform that is used for investment portfolio optimization within a financial ecosystem.
This kind of complex ICT environments need to be secure and trustworthy, as they manage sensitive data which is typically used to improve the investment decisions of companies, and if there were compromised they could impact significantly the investors’ economic health.
The investments optimization platform provides two applications
The first one is related to the training of machine learning models, mostly complex neural networks, in order to offer support to investment funds and companies, to make their investment decisions more effective.
The second one is used for conducting predictions in near real-time.
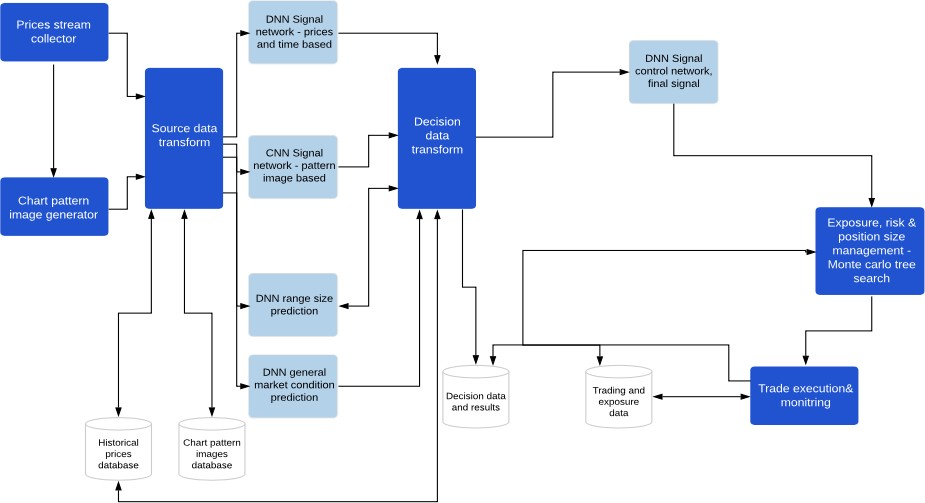
Investment portfolio optimization platform
Employing BIECO’s framework will ensure continuous control and improvement of security related processes within the investments’ platform.
Detecting vulnerabilities
Detecting more accurately software vulnerability that might exist in the software, and determine how a possible vulnerability of the gateway could propagate to the smart grid (WP3).
Auditing and monitoring
Auditing and monitoring the integration with other third party systems and components, as well as the correct runtime behaviour of the gateway and its subsystems (WP5).
Obtaining guarantees
Obtaining guarantees that certify the adherence of the software to its expected behaviour (WP7).
Performing self-checks
Performing self-checks that allow to detect residual vulnerabilities, software and hardware failures; using simulation tools that enable a virtual evaluation when an adversary is influencing clock synchronization (WP4).
Risk assessment
Performing a risk assessment and threat modelling of the status of the system, taking into account also how a gateway vulnerability could impact the smart grid (WP6).
Use Case 3: Smart Microfactory
I-FEVS will provide a smart microfactory platform that is used to produce urban electric vehicles.
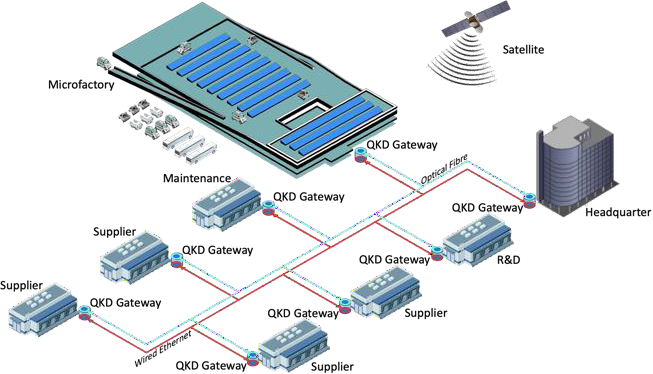
Reliable and adaptable communication infrastructure
The smart microfactory represents an ongoing evolution from traditional factories to a fully connected, flexible and reconfigurable systems that can learn, self-adapt and self-optimize in real or near real-time to frequently changing product and production requirements.
These manufacturing facilities interact and are typically controlled by a number of distributed and networked computing elements, as well as human users. In these environments, having a reliable and adaptable communication infrastructure is critical for achieving agile production systems that enable a high productivity, which impacts directly on the business competitiveness.
Thanks to BIECO, the smart microfactory will obtain a set of advanced security mechanisms that will allow to demonstrate the reliability of its subsystems, especially when they are interacting with the full supply chain. In this case, the relation between security and safety in cyber-physical systems (CPS) will also be demonstrated.

Implementing and testing a quantum secured E-E environment
In order to achieve this, IFEVS aims at implementing and testing a quantum secured E-E environment for connected electric vehicles, addressing also the possibility to extend the solutions to secure the full microfactory and the supply chain.
Therefore, the idea is ensuring the factory assets, so that information is only made available and disclosed to authorized microfactories, and it is fully protected from unauthorized requests. In order to do this, the smart microfactory use case will rely on the following technologies of BIECO’s framework:
Detecting vulnerabilities
detecting accurately vulnerabilities that can be hidden in any of the ICT components of the microfactory, and their propagation across the supply chain (WP3).
Predicting the behaviour
predicting the behaviour of the microfactory regarding security, based on a simulation environment; assessing the trustworthy runtime behavior of the ICT systems of the microfactory; and analyzing how vulnerabilities can propagate through the supply chain (WP5).
Performing self-checks
performing self-checks that allow to detect residual vulnerabilities, software and hardware failures and predicting malicious behaviour of the software components (WP4).
Performing a risk assessment
Performing a risk assessment and threat modelling of the status of the smicrofactory, including also safety aspects (WP6).
Obtaining guarantees
Obtaining guarantees that certify the adherence of the ICT components of the microfactory to their expected behaviour (WP7).
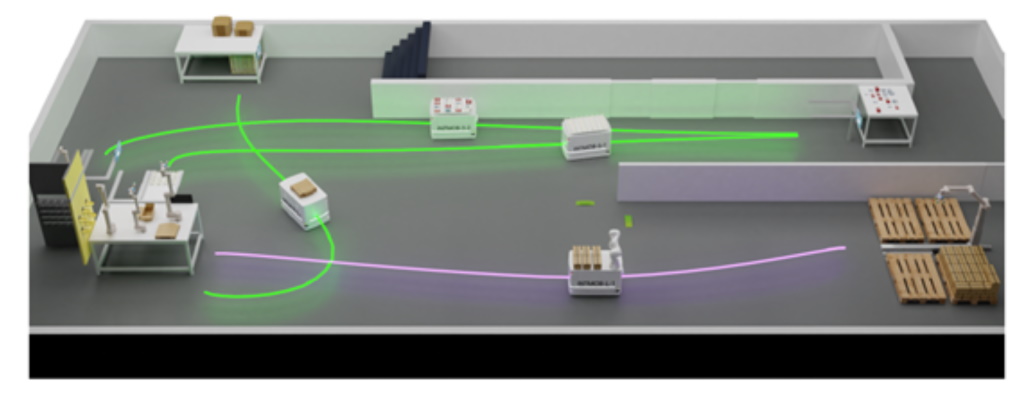
USE CASE 4
Autonomous Navigation Pre-Demo
Autonomous Navigation
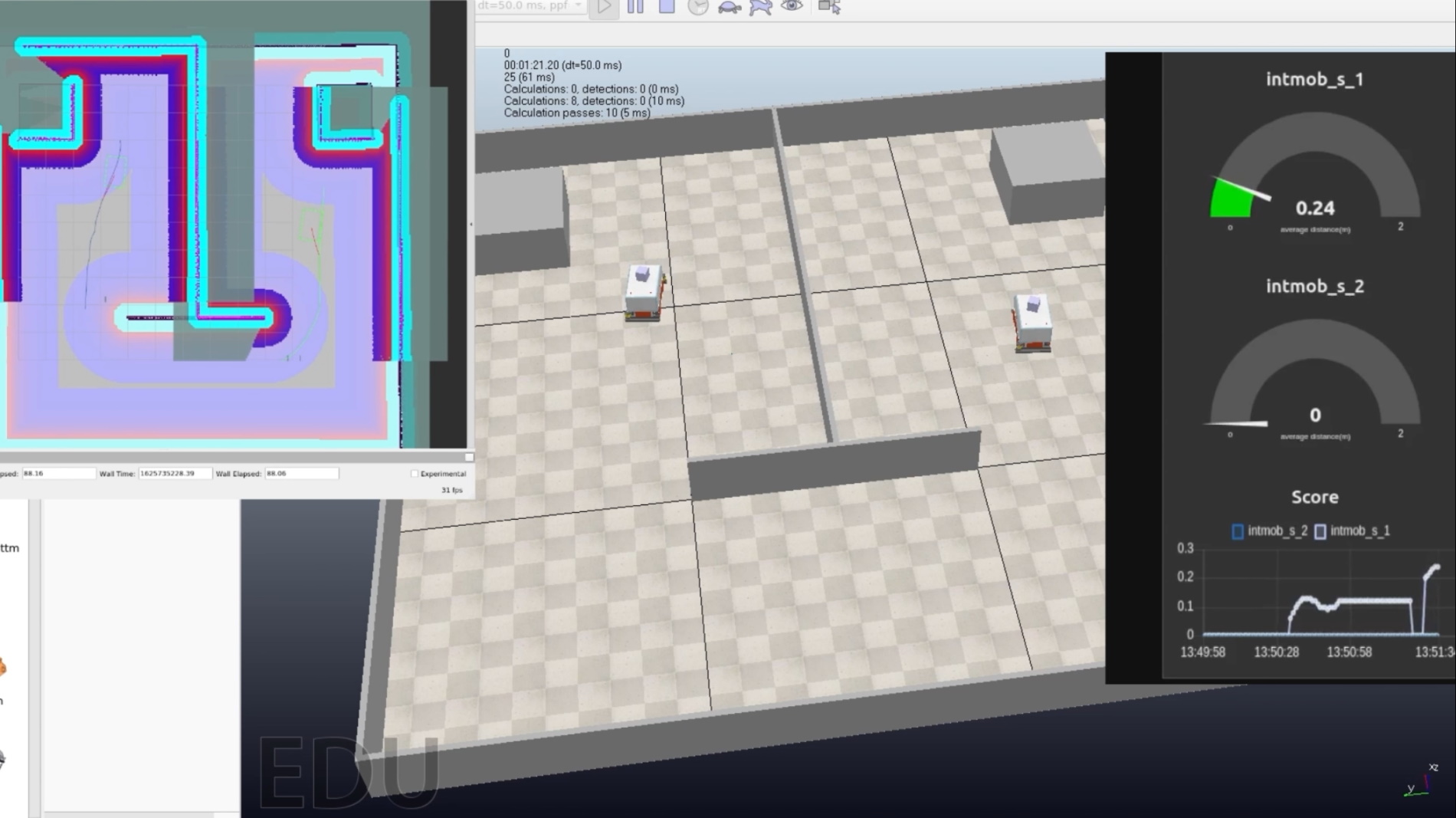
The autonomous navigation use case is meant to serve as a pre-demonstration environment for the internal workshop to be organized around M12. It entails the ensurance of trust and safety in the context of the addition/update of a new module within the navigation environment, more specifically the local planner.
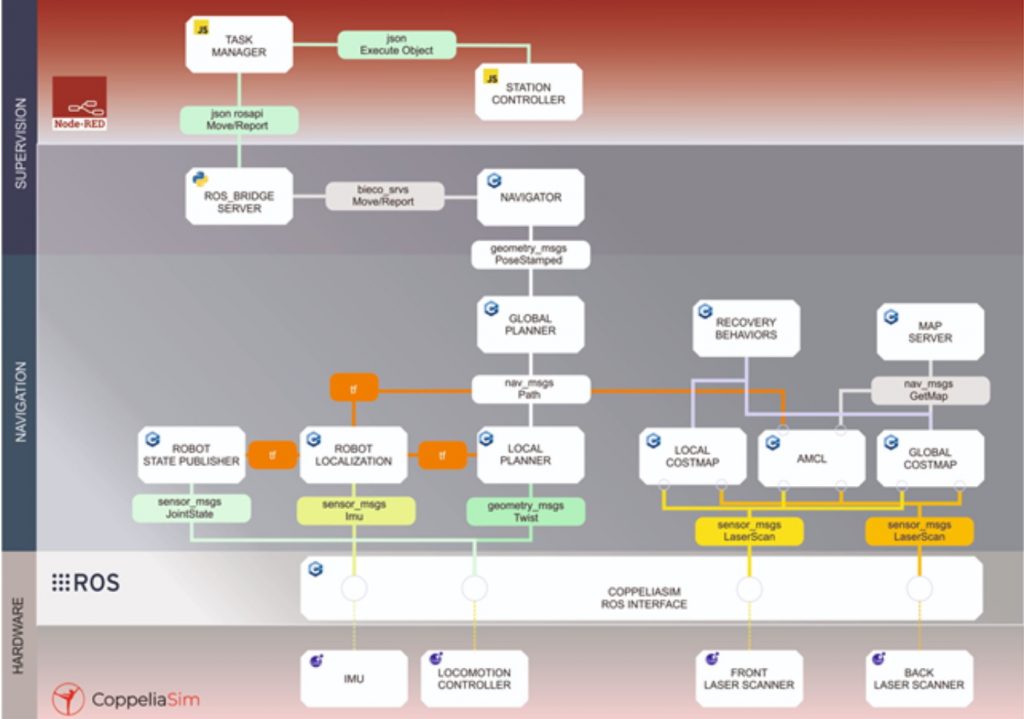
USECASE 4 architecture is organized into three layers
The first is the supervision where the task manager is responsible for transforming the production schedule into action commands to the other entities of the system. Each station has a station controller that receives specific tasks to produce items that will then be transported by the mobile robots. The navigator is the supervisor module of the mobile robots that given instructions from the task manager will control the modules of the navigation layer. In the navigation layer the X,Y position of each goal is sent to the global planner that will produce a plan to reach the aforementioned goal. The plan is the result of the computation of the goal’s final position, direct sensory input and the obstacle information stored in the global costmaps. Based on the global plan, the direct sensory input and the data of the local costmap the local planner will produce motion commands that are sent directly to the locomotion controller.

