WP3 – Vulnerabilities Management
Coordinated by
GRAD (M01-M30)
Objective
This work package has the following objectives:
- Analyze the state of the art to incorporate the latest advances in detection, forecasting and propagation of vulnerabilities
- Compile a representative dataset of software vulnerabilities, taking into account the data provided by BIECO’s use cases as well as from other public sources, and select the most representative features for an effective vulnerability detection process.
- Provide advanced tools to detect and forecast accurately vulnerabilities in ICT systems and components.
- Provide an advanced tool to analyze the propagation of vulnerabilities across the ICT supply chain.
Deliverables
- D3.1 Report on the state of the art of vulnerability management WP3 (5 – GRADIANT) Report Public M6
- D3.2 Dataset with software vulnerabilities WP3 (4 – UTC) Other Confidential, only for members of the consortium (including the Commission Services) M12
- D3.3 Report of the tools for vulnerability detection and forecasting WP3 (5 – GRADIANT) Report Public M18
- D3.4 Report of the tools for vulnerabilities propagation WP3 (5 – GRADIANT) Report Public M21
- D3.5 Updated Report of the tools for vulnerability detection and forecasting WP3 (5 – GRADIANT) Report Public M30
- D3.6 Updated Report of the tools for vulnerabilities propagation WP3 (5 – GRADIANT) Report Public M30
Outcomes
BIECO Project – Methodology for Security Evaluation
We happily announce that BIECO has been presented at @YavaConf 2022! The session entitled "BIECO Project - Methodology for Security Evaluation" has been presented on Tuesday - September 27th, by Marcin Byra, @7bulls.com. The presentation is available here....
2nd Workshop on Accountability, Liability and Trust for 5G and Beyond – Video
Dis you miss the opportunity to attend to the 2nd Workshop on Accountability, Liability, and Trust for 5G and Beyond (WALT5G+)? Don't worry! You can still see the video that D. Sara Matheu presented about the BIECO work performed within WP6. Abstract: While the...
WP3 Monthly meeting July 2022
After the face-to-face meeting of BIECO in June in Lisbon, where useful ideas for the correct development of the tools have been clarified and secured, the regular WP3 monthly meetings have been taken up. In the July meeting, the evolution of the different detection,...
2nd Workshop on Accountability, Liability and Trust for 5G and Beyond
1st International Conference on 6G Networking BIECO participates this Friday 8th july in the 2nd Workshop on Accountability, Liability, and Trust for 5G and Beyond (WALT5G+). This conference provides an interdisciplinary forum to exchange innovative research ideas,...
BIECO first F2F meeting
BIECO Progress Meeting Agenda 7-9th June 2022, 09:00- 17:00 WET Location: UNINOVA – Building 1 – Campus da FCT-UNL, Quinta da Torre, 2829-516 Caparica Meeting Objectives: 1. Analysing the Review Meeting 2. Align the view of the...
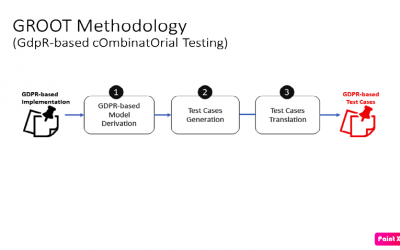
GROOT: GdpR-based cOmbinatOrial Testing strategy (BIECO Version)
Short description In this video, the CNR presents GROOT, a generic combinatorial testing methodology specifically conceived for assessing compliance with the GDPR and its contextualization in the context of the access control domain, considering the peculiarity of the...