WP4 – Development of Resilient Systems
Coordinated by
IESE (M01-M36)
Objective
In this WP, tools and methods will be developed for supporting creation of resilient systems w.r.t security attacks and vulnerabilities. The scope is to develop systems that can cope with behavior disturbances caused by malicious attacks, that manifest into a loss of control and can bring a system into hazardous situations. A resilient system shall be able to compensate for interruptions and get back into a safe state in case of emergency situations caused by malicious attacks. In this regard the system shall be able to autonomously and automatically construct awareness of its security in a dynamic environment, to recognize critical situations and to identify the right operational mode for remaining into a secure and trusted operational state.
Concretely, this work package has the following objectives:
- To develop methods and tools that enable runtime evaluation of system operational state in dynamic environments.
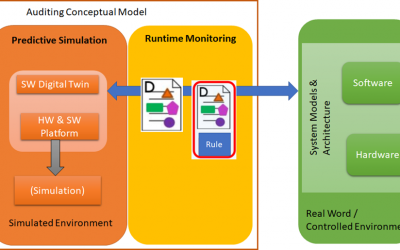
- To enhance existing tools that can predict failure propagation caused by malicious attacks and support the transition of an ICT system into a resilient state. Prediction is performed in a simulated environment by counteracting the capabilities of the system under evaluation to detect that it is under evaluation.
- To develop methods that during runtime bring a system into a safe, trusted state, making it resilient to malicious attacks.
Deliverables
- D4.1 Report on Self-checking of vulnerabilities and failures WP4 (7 – RESILTECH) Report Confidential, only for members of the consortium (including the Commission Services) M30
- D4.2 Report on methods and tools for the failure prediction WP4 (2 – Fraunhofer) Report Confidential, only for members of the consortium (including the Commission Services) M24
- D4.3 Report on Method development for resilient systems WP4 (2 – Fraunhofer) Report Confidential, only for members of the consortium (including the Commission Services) M30
Outcomes
A comparative study of the most important methods for forecasting the ICT systems vulnerabilities
Authors: Ovidiu Cosma, Mara Hajdu-Macelaru, Petrica Pop-Sitar, Cosmin Sabo, Ioana Zelina
Comparison of Safety and Security analysis techniques
Authors: Emilia Cioroaica, Smruti Ranjan Kar, and Ioannis Sorokos
BIECO Runtime Auditing Framework
Authors: Antonello Calabro, Emilia Cioroaica, Said Daoudagh, and Eda Marchetti
Goals within Trust-based Digital Ecosystems
Authors: Emilia Cioroaica, Akanksha Purohit, Barbora Buhnova, and Daniel Schneider
Bridging Trust in Runtime Open Evaluation Scenarios
Authors: Emilia Cioroaica, Barbora Buhnova, Eda Marchetti, Daniel Schneider, and Thomas Kuhn
BIECO M12 Progress Meeting
BIECO M12 Progress Meeting Agenda 7-8th September 2021, 09:00- 15:00 CET Location: Teams – General Meeting Objectives: Check the progress statusAlign the work in all WP’sAlign the view of the participants with the vision of the project Attendees: Representatives of...