WP5 – Methods and Tools for Auditing complex systems
Coordinated by
CNR (M04-M30)
Objective
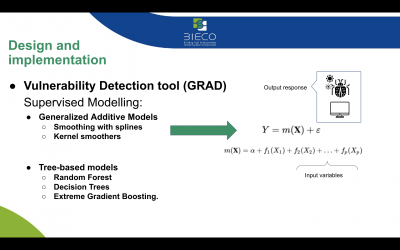
This work package will focus on the development of techniques, methods and tools supporting the audit activity in the BIECO framework. Auditing includes retrieval of data from the field, such as data regarding the usage mode of an ICT system subject to runtime adaptation through the delivery of software updates. The main goal is to provide ecosystem trustworthiness’s evaluation leveraging executable simulation environments and runtime monitoring facilities. The monitoring results aim to provide useful feedback for setting up the simulation environment.
This work package has the following objectives:
- Definition of the executable simulation models and of the parameters against which the behavior of the ICT systems and their interacting actors within an ecosystem is judged as being trustworthy or not.
- Definition of monitoring methodologies and tools detecting malicious behaviors of ICT systems and interacting actors within the ecosystems and assessing the validity of the simulation models.
- Developing monitoring tools able to validate through real-time data of systems sensors and actuators the validity of simulation decisions.
Deliverables
- D5.1 Definition of the simulation model and monitoring methodologies WP5 (3 – CNR) Report Confidential, only for members of the consortium (including the Commission Services) M12
- D5.2 First version of the simulation environment and monitoring solutions WP5 (3 – CNR) Report Public M24
- D5.3 Final version of the simulation environment and monitoring tools WP5 (2 – Fraunhofer) Report Public M30
Outcomes
Monthly Wp3 meeting
BIECO WP3On November the 30th, it was taken the monthly Wp3 meeting. On it, it was updated the latest progress as well as future actions, and all WP3 members were coordinated in order to achieve the programmed objective.These advances were centered on both tasks T3.3...
WP7 monthly meeting M15
The 29th November took place the WP7 monthly meeting. As part of T7.3 we tried to instantiate and coordinate the different steps of the security evaluation methodology being developed in T7.2.
The BIECO Conceptual Framework Towards Security and Trust in ICT Ecosystems
The BIECO Conceptual Framework Towards Security and Trust in ICT Ecosystems Authors: Ricardo Peres, Lilian Adkinson, Emilia Cioroaica, Eda Marchetti, Enrico Schiavone, Sara Matheu, Ovidiu Cosma, Radoslaw Piliszek, Jose Barata Document type: Publication in Conference...
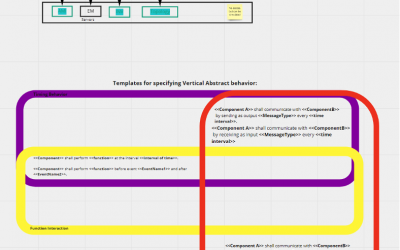
25th Nov – ICT Gateway
In the meeting on the 25th of November, we have defined templates for specifying vertical abstractions of components interacting with the ICT Gateway. When fed with real-time data, these abstractions become digital twins that are predictively evaluated in a simulation...
A MDE Tool for Security Risk Assessment of Enterprises
A MDE Tool for Security Risk Assessment of Enterprises Authors: Enrico Schiavone, Nicola Nostro, Francesco Brancati Document type: Publication in Conference proceedings Publication: INDUSTRY TRACK - LATIN-AMERICAN SYMPOSIUM ON DEPENDABLE COMPUTING (LADC), 10. , 2021,...
WP2 activities November
During November, WP2 partners have been refining the representations of data flows and component structures of the BIECO framework, which will be some of the core elements included in Deliverable 2.4. Even in the remote setting, interesting discussions have been...